The AMTSO web site has a “Feature Settings Check” page that includes links to several files to test security applications. The standard EICAR file, as well as a few additional executable files.
Wednesday, July 1, 2015
Export-WindowsDriver
Windows 8.1 Update 1 includes a new PowerShell cmdlet with the name of Export-WindowsDriver. This cmdlet can export installed third-party drivers of an existing Windows computer. An example would be:
Export-WindowsDriver –Online -Destination c:\export-drivers
The output should contain existing drivers in separate subfolders.
Basic information on Windows Server 2012 R2 Core
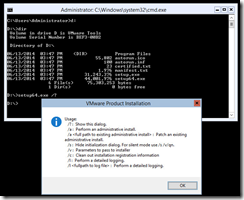
Below is some basic information on configuring a new Windows Server 2012 R2 Core installation. If installing the new server within VMware, use the menu option as normal to install/update VMware Tools. Launch a command prompt and use the following command via the D: drive or whatever drive letter the CD-ROM is mapped to. The server should restart automatically.
Setup64.exe /s /v /qn
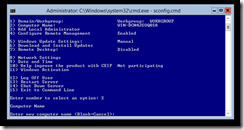
To perform some basic configuration, the sconfig.cmd command will display a menu list of various tasks.
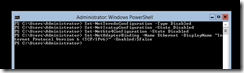
A PowerShell prompt can be launched by simply using the command powershell. Below are some examples of disabling the tunneling protocols and IPv6.
Set-NetTeredoConfiguration -Type Disabled
Set-NetIsatapConfiguration -State Disabled
Set-Net6to4Configuration -State Disabled
Set-NetAdapterBinding -name <NIC name> -DisplayName "Internet Protocol Version 6 (TCP/IPv6)" -Enabled:$false
Parrot Security OS
Parrot Security OS is a security oriented operating system designed for Penetration Testing, Computer Forensic, Reverse engineering, Hacking, Privacy/Anonymity and Cryptography. It is based on Debian and developed by Frozenbox network.
Checking The Health Of a Domain Controller After Promotion
After a Windows Server is promoted to a domain controller, these are some steps to verify all components are functioning properly.
Check inbound and outbound AD replication by using the command -> REPADMIN /SHOWREPL /REPSTO
If the DC is a Global Catalog Server, check it has finished the build of the GC partitions and it is advertising itself as such by using the command -> Get-WinEvent -LogName "Directory Service" | ?{$_.Id -eq 1119} | fl
Check the SYSVOL has been initialized and finished initial replication by using the command -> Get-WinEvent -LogName "DFS Replication" | ?{$_.Id -eq 4604} | fl
To obtain additional details, run the command -> DCDIAG /C /D /V
Kansa
Kansa is a modular incident response framework written in Powershell.
https://github.com/davehull/Kansa/
Once downloaded and extracted, use the following command to “unblock” the .PS1 files.
ls -r *.ps1 | Unblock-File
The main purpose of the framework is to use PowerShell Remoting to obtain information from several clients. Several pre-built scripts such as for Netstat are available that can be executed as standalone.
RBAC Manager R2 for Exchange 2010/2013
RBAC Manager is a tool to simplify RBAC administration. Basically it provides the missing GUI to edit RBAC settings on Exchange 2010 systems; including adding/removing cmdlets, cmdlet properties, assignments etc.
File Permissions Check
File Permissions Check is an utility to scan all files in a folder structure and report the files that do not have permissions that are identical to those of their parent folder. After the tool locates such files, you can either use the tool to “fix” the permissions (by setting them back to inheriting and, optionally, removing any explicit permissions) or you can simply right-click them and open their properties in Explorer to look at their exact permissions.