Below is a link to a KB article concerning the issue of Microsoft’s Office Isolated Conversion Environment for Office. MOICE uses the 2007 Microsoft Office system converters to convert the Office binary format files into the Office Open XML format. This process helps remove the potential threat that may exist if the document is opened in the binary format. Additionally, MOICE converts incoming files in an isolated environment.
Sunday, May 2, 2010
How to enable DEP for Microsoft Office
Below is a link to a KB article concerning the issue of enabling DEP with Microsoft Office.
How to manually troubleshoot and repair the Windows 7 bootloader
Below are some steps and a link concerning the bootrec.exe file with Windows 7. This option should be used after attempting to perform a “normal” repair via the Windows 7 disk.
1. Boot the machine in question via the Windows 7 installation disk.
2. Press a key when you are prompted.
3. Click Repair your computer.
4. Click on the operating system that you wish to repair and click Next.
5. In the System Recovery Options dialog box, click Command Prompt.
6. Type bootrec.exe.
The bootrec.exe /FixMbr writes a MBR to the system partition.
The bootrec.exe /FixBoot writes a new boot sector to the system partition.
The bootrec.exe /ScanOs scans all disks for installations that are compatible with Vista or Windows 7.
The bootrec.exe /RebuildBcd allows you to select the installations that you wish to add to the BCD store.
More information can be found at the link below:
Loverboy security tool
Loverboy is a web application penetration testing tool that can extract data from SQL Server, MySQL, DB2, Oracle, Sybase, Informix, and Postgres. Further, it can crawl a website as a vulnerability scanner looking for sql injection vulnerabilities.
Detecting an IP address conflict with Microsoft’s DHCP Server
An IP address conflict detection option can be enabled within Microsoft’s DHCP Server software by accessing the Properties of the node and setting the Conflict Detection Attempts to a value other than 0.
A value other than 0 will mean the server will send a ping request for the address in question before assigning it.
SetACL
SetACL is a set of routines for managing Windows permissions (ACLs) from the command line, from scripts and from programs.
Netsparker Community Edition
NetSparker Community Edition is a free version of a web application security scanner.
SFX-SQLi
SFX-SQLi (Select For XML SQL injection) is a new SQL injection technique which allows to extract the whole information of a Microsoft SQL Server 2005/2008 database in an extremely fast and efficient way.
This technique is based on the FOR XML clause, which is able to convert the content of a table into a single string, so its contents could be appended to some field injecting a subquery into a vulnerable input of a web application.
Microsoft Touch Pack for Windows 7
The Microsoft Touch Pack for Windows 7 is a collection of games and applications that are made available to computers with multi-touch enabled displays running Windows 7.
Souptoys
Souptoys is a unique toy box for your desktop that includes 100 interactive desktop items that can be used to effectively waste your spare time or to keep kids entertained for hours. Simply drag an item out of the toy box and interact with it by throwing, pushing, stacking or other means. Each item will behave according to the laws of physics. You can use basketballs, robots, wooden blocks, cannons, flying bees, magnets, pirate ships, guide rails, gear wheels and many other items to create chain reactions, complex machines or to build a castle and blow it to pieces with your canon. Souptoys allows you to save your creations as playsets and also includes dozens of sample playsets that you can use for inspiration. Designed for kids 5-12, but fun for everyone who has too much spare time on their hands.
Universal USB Installer
Universal USB Installer is a Live Linux USB Creator that allows you to choose from a selection of Linux Distributions to put on your USB Flash Drive. The Universal USB Installer is easy to use. Simply choose a Live Linux Distribution, the ISO file, your Flash Drive and, Click Install. Other features include; Persistence (if available), and the ability to format the flash drive (recommended) to ensure a clean install. Upon completion, you should have a ready to run bootable USB Flash Drive with your select Linux version installed.
http://www.pendrivelinux.com/universal-usb-installer-easy-as-1-2-3/
WinCDEmu
WinCDEmu is an open-source software that allows mounting CD/DVD images by clicking at the image files in Windows Explorer.
Bonkey
Bonkey is a simple to use backup system. It can backup to most storage devices, but it is specifically designed to be used with Amazon S3. You choose which files need to be backed up, select how often, set the destination and your files are backed up. It runs on Windows and Mac OSX.
Roadkil.net
Roadki.net is a web site that contains downloads for several different categories. Topics include networking, disk, security, etc.
PowerShell in Bing Visual Search
To view PowerShell Cmdlets in Bing Visual Search:
1. Go to Bing: http://www.bing.com.
2. From the menu on the left, click Visual Search.
3. Click Reference, and scroll down to Scripting.
4. Click Windows PowerShell Cmdlets
PowerShell Startup Options
Here is a listing of the available startup options for PowerShell:
-Command Specifies the command text to execute as though it were typed at the PowerShell command prompt.
-EncodedCommand Specifies the base64-encoded command text to execute.
-ExecutionPolicy Sets the default execution policy for the console session.
-File Sets the name of a script file to execute.
-InputFormat Sets the format for data sent to PowerShell as either text string or serialized XML. The default format is XML. Valid values are text and XML.
-NoExit Does not exit after running startup commands. This parameter is useful when you run PowerShell commands or scripts via the command prompt (cmd.exe).
-NoLogo Starts the PowerShell console without displaying the copyright banner.
-Noninteractive Starts the PowerShell console in non-interactive mode. In this mode, PowerShell does not present an interactive prompt to the user.
-NoProfile Tells the PowerShell console not to load the current user’s profile.
-OutputFormat Sets the format for output as either text string or serialized XML. The default format is text. Valid values are text and XML.
-PSConsoleFile Loads the specified Windows PowerShell console file. Console files end with the .psc1 extension and can be used to ensure that specific snap-in extensions are loaded and available. You can create a console file using Export-Console in Windows PowerShell.
-Sta Starts PowerShell in single-threaded mode.
-Version Sets the version of Windows PowerShell to use for compatibility, such as 1.0.
-WindowStyle Sets the window style as Normal, Minimized, Maximized, or Hidden. The default is Normal.
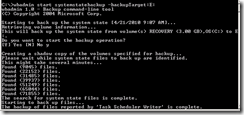
Back up the System State with Windows Server 2008 R2
To back up the system state with Windows Server 2008 R2, install the Backup feature. Then launch a command prompt and use:
wbadmin start systemstatebackup –backupTarget:VolumeName
Penetration Testing Linux Distributions
Below are some Linux distributions designed for penetration testing.