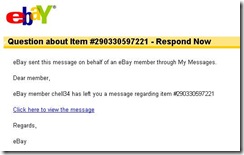
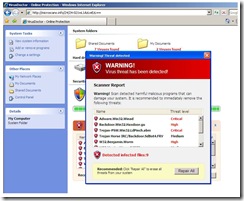
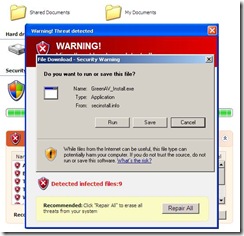
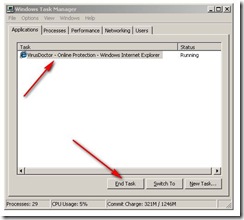
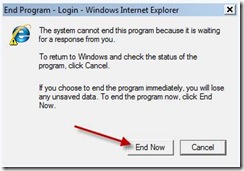
One change Microsoft started with Vista and continued with Windows 7 is to remove some components and make them available via a separate download. This was done to remove some “size” from Windows and to allow faster development for some of the applications in question.
To download and install some or all of these applications, access:
Once on the home page, click on the Download button. A separate link is available under the Download button for system requirements. Some of the components will run under Windows XP but others such as Movie Maker will not.
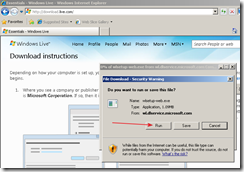
When a file dialog box appears, click on the Run button.
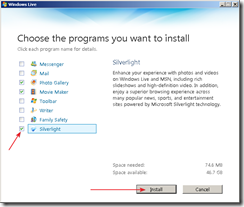
After downloading the initial loader, a dialog box will appear asking which applications you wish to install. When you click on an entry, a description of the component should be displayed on the right. After selecting the applications, click on the Install button.
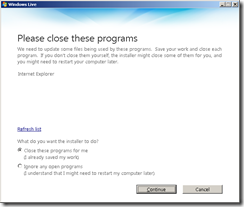
A dialog box may appear asking to close some open programs; click on the Continue button if all data has been saved.
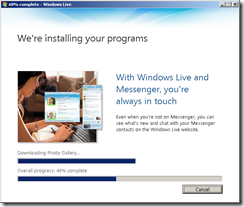
Depending on the components selected and your Internet speed, the download and installation can take a few or several minutes.
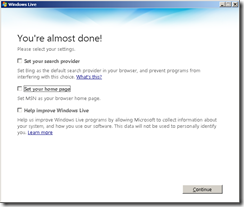
One of the final screens ask to change your home page and search engine; you have the option of not making these changes. Once you have made your selections, click on the Continue button.
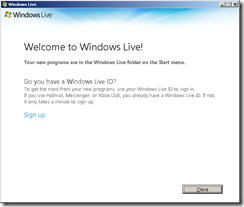
The install process should now be completed. Click on the Close button.
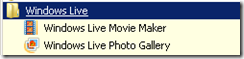
To access some of the applications, a new Windows Live entry should now be present under the Start Menu.
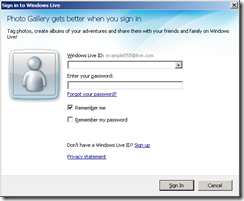
When you open some of the applications, a dialog box may appear asking to log into Live.com:
You can use an existing Live.com account or create a new entry if you wish. But a Live.com account is not a requirement for using the application. In the example above, you could simply click on the Cancel button and continue to use the program.


![clip_image004[4] clip_image004[4]](http://lh6.ggpht.com/_MRc-S-tl3G8/Sresadjx4zI/AAAAAAAAAFA/StxYCYYuTM8/clip_image004%5B4%5D_thumb.jpg?imgmax=800)