Below are some examples of different Show commands within Cisco’s IOS.
show version
The command show version provides basic information about the device in question, such as hardware resources, software revision, and uptime.
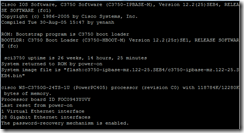
show inventory
The command show inventory provides a compiled list of all hardware components present in the device in question, such as a description, part ID, hardware revision, and serial number.
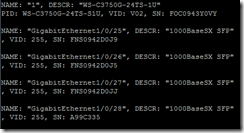
show environment
The command show environment displays hardware diagnostic information such as power supply status, fan speed, and temperatures.
show tech-support
The command show tech-support is an alias for a number of other commands and it will create a large amount of information that can be submitted with a support request.
show processes
The command show processes displays running processes on the device in question.
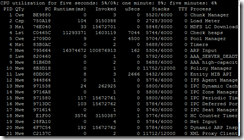
A similar command of show processes cpu sorted can be used to determine the processes by the highest CPU utilization.