Tuesday, December 2, 2014
Obtaining Installation Media for Windows 8.1
The link below offers an utility to create installation media for Windows 8.1. Once downloaded and executed, the application will ask a few questions such as 32-bit vs. 64-bit. The user account in question must be a member of the local Administrators group before the utility will launch correctly.
http://windows.microsoft.com/en-us/windows-8/create-reset-refresh-media
ABC-Update
ABC-Update is a free utility from ABC-Deploy. It can be used as a standalone tool, or in conjunction with software distribution tools like ABC-Deploy, MS SCCM and others. ABC-Update.exe is a command line tool that sets you in control of MS Update operations.
Arachni
Arachni is an Open Source, feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications.
AD ACL Scanner
AD ACL Scanner is a PowerShell script. Once executed, it will display a graphical interface. The utility will create reports of access control lists (DACLs) and system access control lists (SACLs) in Active Directory.
Monday, December 1, 2014
CipherShed
CipherShed is a free encryption software that started as a fork of the now-discontinued TrueCrypt Project. CipherShed will be available for Windows, Mac OS, and GNU/Linux.
Justniffer
Justniffer is a network protocol analyzer that captures network traffic and produces logs in a customized way, can emulate Apache web server log files, track response times and extract all "intercepted" files from the HTTP traffic.
Sunday, November 2, 2014
PowerShell commands to disable IPv6
The following PowerShell commands can be used to disable the default tunneling IPv6 protocols.
Set-NetTeredoConfiguration -Type Disabled
Set-NetIsatapConfiguration -State Disabled
Set-Net6to4Configuration -State Disabled
The following command will disable IPv6 for a particular NIC.
Set-NetAdapterBinding -name <NIC name> -DisplayName "Internet Protocol Version 6 (TCP/IPv6)" -Enabled:$false
AutoAdministrator
AutoAdministrator lets you query or update a variety of Windows settings and services across any number of servers and/or workstations, without the need to create a script or perform the actions manually.
How to reduce the glare within iOS
To reduce the glare or brightness within iOS, access Settings -> General -> Accessibility -> Increase Contrast. Two settings to verify would be:
Darken Colors –> This darkens the menu font by changing it from light blue to dark blue.
Reduce White Point –> This darkens the whitest white that iOS will display and tunes down the glare.
MagicTree
MagicTree is a penetration tester productivity tool. It is designed to allow easy and straightforward data consolidation, querying, external command execution and report generation.
Options for running a honeypot on a Raspberry Pi
A recent blog posting discussed running a honeypot on a Raspberry Pi using the Raspbian operating system http://www.raspbian.org/ as the base. Below are a few different options that were listed as potential honeypot services.
Saturday, November 1, 2014
Mail Protection Reports for Office 365
Mail Protection Reports for Office 365 is an add-on for Excel to obtain more detailed information on email traffic within Office 365.
http://www.microsoft.com/en-us/download/details.aspx?id=30716
SELKS
SELKS is a specialist Debian-based distribution that ships with a variety of pre-configured network security management tools.
Bitnami
Bitnami is a library of popular server applications and development environments that can be installed with one click, either in your laptop, in a virtual machine or hosted in the cloud. We take care of compiling and configuring the applications and all of their dependencies (third-party libraries, language runtimes, databases) so they work out-of-the-box.
PowerShell cmdlets included with Message Analyzer
Several PowerShell cmdlets are included within the installation of Message Analyzer. Once installed, launch an elevated PowerShell session and issue the Update-Help command. Then use Get-Help per to view the available cmdlets.
One option available is to perform a capture in a circular method, which allows the trace to continue while dropping older data.
More information can be found at the following links:
Saturday, October 4, 2014
Sites that can parse email message headers
The following web sites have an option available to paste in email message headers for analysis.
https://testconnectivity.microsoft.com/
Shortcut to launch the ISE while within a PowerShell session
To launch the ISE (Integrated Scripting Environment) while within a PowerShell session, simply type “ise” and hit the Enter key. A new window with the ISE should open.
View Auditing Portal
View Auditing Portal is a fling that web portal that serves as an extension to Horizon View Administrator. It offers additional information such as showing parent virtual machines of linked clone desktop pools and descendant snapshots in a tree view.
How to open online help within PowerShell
To open a web page with documentation on a particular cmdlet or command within PowerShell, use the format Get-Help cmdlet –Online. The default web browser should open to the online documentation for the cmdlet in question.
Microsoft Azure Cost Estimator Tool
Microsoft Azure Cost Estimator Tool is an installable tool to profile existing on-premises infrastructure and then estimates the cost of running apps and services in the Microsoft Azure Cloud. The tool supports virtualization solutions Hyper-V, System Center Virtual Machine Manager, vCenter, and ESXi and supports Windows and Linux physical machines.
http://www.microsoft.com/en-us/download/details.aspx?id=43376&WT.mc_id=rss_alldownloads_all
OSSEC
OSSEC is an Open Source Host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.
NetAdapter Repair
NetAdapter Repair is an All In One program that allows a user to effectively troubleshoot and repair common problems with networking adapters within Windows.
Thursday, October 2, 2014
Intercepter-NG
Intercepter-NG is a multifunctional network toolkit for various types of IT specialists. The main purpose is to recover *interesting* data from the network stream and perform different kinds of MiTM attacks.
PowerActions
PowerActions integrates the vSphere Web Client and PowerCLI to provide complex automation solutions from within the standard vSphere management client. PowerActions is deployed as a plugin for the vSphere Web Client and will allow you to execute PowerCLI commands and scripts in a vSphere Web Client integrated Powershell console.
https://labs.vmware.com/flings/poweractions-for-vsphere-web-client
ZAProxy
ZAProxy or OWASP Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
VMware I/O Analyzer
VMware I/O Analyzer is an integrated framework designed to measure storage performance in a virtual environment and to help diagnose storage performance concerns. I/O Analyzer, supplied as an easy-to-deploy virtual appliance, automates storage performance analysis through a unified interface that can be used to configure and deploy storage tests and view graphical results for those tests.
Tuesday, September 2, 2014
Create a text file of installed updates and hotfixes within Windows
To obtain a text file that contains a list of installed updates and hotfixes from within Windows, launch an elevated command prompt and use the following command:
wmic qfe list brief /format:texttablewsys > list.txt
Right-click options with the Outlook 2013 system tray icon
Several menu options are available when the right-clicking the system tray icon when Outlook 2013 is open:
But two additional options are available if the Control Key is held when right-clicking the system tray icon.
PoshWSUS
PoshWSUS is a PowerShell module for Microsoft’s Windows Server Update Services (WSUS) that offers command-line options for managing the service.
ViewDbChk
The ViewDbChk tool allows administrators to scan for, and fix provisioning errors that can not be addressed using View Administrator. Provisioning errors occur when there are inconsistencies between the LDAP, vCenter and View Composer databases. These can be caused by: direct editing of the vCenter inventory, restoring a backup, or a long term network problem.
This tool allows VMware View administrators to scan for machines which can not be provisioned and remove all database entries for them. The View Connection Server will then be able to re-provision the machine without any errors.
HoneyDrive
HoneyDrive is a honeypot Linux distro. It is a virtual appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed. It contains over 10 pre-installed and pre-configured honeypot software packages, as well as many useful pre-configured scripts and utilities to analyze, visualize and process the data it can capture.
IronWASP
IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability testing.
GlassWire
GlassWire is a network security monitoring utility for Windows. GlassWire displays your network activity on an easy to understand graph while searching for unusual Internet behavior that could indicate malware or violations of your privacy.
How to add new items to the Send To Context Menu within Windows
To add a new item or destination to the Send To Content Menu within Windows, launch the Run dialog box (Windows key + R) and enter:
shell:sendto
The SentTo folder should open up within Windows Explorer. To add a new item, right-click within the dialog box and use the New –> Shortcut option.
How to remove a cached email address within the Windows 8.1 Mail application
By default, the Windows 8.1 Mail application caches autocomplete email addresses. It can be difficult to remove these cached entries from the application. The YouTube video below discusses one procedure to remove them.
https://www.youtube.com/watch?v=kq0-fZd0xpI&feature=youtu.be
CrowdStrike Inspect
CrowdStrike has several free utilities available at http://www.crowdstrike.com/community-tools/. One example would be Crowd Inspect, an application that is a host-based process inspection tool utilizing multiple sources of information to detect untrusted or malicious network-active process.
Saturday, August 2, 2014
Using the “Run as different user” command prompt option with Windows 8.1/Windows Server 2012 R2
In versions prior to Windows 8.1, it was possible to hold down the Shift key while right-clicking the shortcut to a Command Prompt to find the option to launch using different credentials. Using the new “Modern” interface with Windows 8.1/Windows Server 2012 R2, this option is not present.
One method to again use this feature is to add a shortcut to the Command Prompt to the task bar on the Desktop. Using the old method of holding down the Shift key while right-clicking the shortcut should display the selection.
WizTree
WizTree is an utility that scans your entire hard drive and shows you which files and folders are using the most disk space. It only works with local NTFS format hard drives. A portable version is available for download.
BlackArch Linux
BlackArch Linux is an Arch Linux-based distribution designed for penetration testers and security researchers. It ships with over a thousand specialist tools for penetration testing and forensic analysis.
Compliance Checker for vSphere
The Compliance Checker for vSphere is a fully-functional product that provides detailed compliance checks against the VMware vSphere Hardening Guidelines.
Friday, August 1, 2014
FakeNet
FakeNet is a tool that aids in the dynamic analysis of malicious software. The tool simulates a network so that malware interacting with a remote host continues to run allowing the analyst to observe the malware’s network activity from within a safe environment.
How to check the status of BitLocker
To check the status of BitLocker, launch an elevated command prompt and use the command:
manage-bde –status
This command should return details such as the version number and the encryption type.
Lightweight Portable Security
Lightweight Portable Security (LPS) creates a secure end node from trusted media on almost any Intel-based computer (PC or Mac). LPS boots a thin Linux operating system from a CD or USB flash stick without mounting a local hard drive.
BinaryTides
BinaryTides is a web site that contains how-to and walk-through articles for different topics for several different Linux distributions.
Friday, July 4, 2014
Sysdig
Sysdig is an open source Linux system troubleshooting tool that captures system state and activity from a running Linux instance. Sysdig captures system calls and other system level events using a Linux kernel facility called tracepoints, which means much less overhead than strace. It then “packetizes” this information, so that you can save it into trace files and filter it, a bit like you would do with tcpdump.
To install it, use the following command:
curl -s https://s3.amazonaws.com/download.draios.com/stable/install-sysdig | sudo bash
Monitoring applications
Below are links to several monitoring applications. Some are based on Nagios, while some offer both free and paid versions.
ELSA
ELSA is a centralized syslog framework built on Syslog-NG, MySQL, and Sphinx full-text search. It provides a fully asynchronous web-based query interface that normalizes logs and makes searching billions of them for arbitrary strings as easy as searching the web. It also includes tools for assigning permissions for viewing the logs as well as email based alerts, scheduled queries, and graphing.
https://code.google.com/p/enterprise-log-search-and-archive/
Script Browser for Windows PowerShell ISE
Script Browser is an add-on for the Windows PowerShell ISE that embeds a special pane directly into the ISE to allow searching through the script samples available in the TechNet Script Center.
http://www.microsoft.com/en-us/download/details.aspx?id=42525&WT.mc_id=rss_alldownloads_all
Ammyy Admin
Ammyy Admin is a remote access utility for Windows. It is free of charge for non-commercial use.
RackTables
RackTables is an free application for server room asset management. It helps document components such as hardware assets, network addresses, space in racks, and network configurations.
Tuesday, July 1, 2014
Bittorrent Sync
Bittorrent Sync is a free syncing tool for computers and mobile devices. The installation is rather standard.
If this is the initial installation, select the standard setup.
Select the sync folder.
Use the default secret value or use your own. A secret is a key that connects different devices and joins them together. The application will automatically generate a secret to ensure their uniqueness. After a folder is added to BitTorrent Sync, the secret is stored in its advanced preferences and can be accessed by right-clicking on a folder in the 'Folders' tab.
There are 3 types of Secrets: master (full access) secret, read only secret for one-way sync and one-time secrets (both full access and read-only). Read only and one-time secrets may be generated only for folders operated by master secrets.
The local client has several tabs available.
A few default files and folders are present under the sync folder.
When you add a new folder to BitTorrent Sync, a number of hidden files/folder are automatically created in the folder. The purpose of each are as follows:
.SyncID = A file containing the unique, internal "ID" of the folder. This file should not be manually modified, or deleted. If you do, the folder will no longer be recognized in BitTorrent Sync.
.SyncIgnore = A user editable file allowing you to "exclude" certain files/sub folders for being sync'd
.SyncArchive = BitTorrent Sync, by default, won't actually delete any of your files/folders. If a corresponding file/folder is deleted on another device, it will simply be "moved" into the .SyncArchive folder on all other devices, rather than being permanently deleted. (In Sync pre v1.1.40, this folder was named .SyncTrash and was later renamed to .SyncArchive as this folder now stores both local files deleted on remote devices, as well as "versioned" files)
.!Sync files = Temporary files created by BitTorrent Sync when receiving incoming data transfers. Once a file is fully received, it is then renamed to have its .!Sync extension removed i.e. "file.mp3" will become "file.mp3.!Sync" on receiving devices until all data for the file is fully received, at which point it will be renamed back to "file.mp3".
.SyncOld = Usually contains a backup of a file when that file gets transferred to your device partially from another location. After the transfer is successful, the .syncold file gets moved to .SyncArchive folder (if allowed in settings).
From v1.1.30 onwards, deleted files are kept in .SyncArchive (or .SyncTrash pre v1.1.40) for a default period of 30 days, after which they will be automatically removed. You can change this default period by adjusting the advanced "sync_trash_ttl" setting.
The secret value can be obtained by right-clicking on the sync folder within the client.
The option of connecting a mobile device will display a QR code to allow for easy configuration.
If you are concerned about security, BitTorrent Sync provides opportunity to regularly generate new Secrets for a folder, or replace an existing secret with your own Base64 string more than 40 characters long. The new folder secret should be re-entered on all the devices in sync.
Syncing happens in real time. In addition, as a fall back, BitTorrent Sync also rescans files/folders every 10 minutes by default. If you're running BitTorrent Sync 1.1.12 (or later), you can now configure this interval via the advanced "folder_rescan_interval" setting (default value is "600" (seconds) = 10 minutes)
The main listening port can be found under the Preferences tab.
Several additional UDP ports will be present as well.
IOMeter
IOMeter is an open source tool originally developed by Intel that remains the simplest and best means of generating load on a system for performance analysis. The utility can be used to test network storage array performance.
Wifislax
Wifislax is Slackware-based live CD with an extensive collection of tools for performing wireless connection analyses and related security tests, although it can equally serve as a general-purpose desktop Linux distribution with a choice of KDE or Xfce desktops. Wifislax has the integration of various unofficial network drivers into the Linux kernel, thus providing out-of-the-box support for a large number of wired and wireless network cards.
VyOS
VyOS is a community fork of Vyatta, which is a Linux-based network operating system that provides software-based network routing, firewall, and VPN functionality.
Sunday, June 1, 2014
Checking the status of the Trusted Platform Module
To check the status of the Trusted Platform Module, launch an elevated command prompt. Use the command below to see if TPM is enabled.
wmic /namespace:\\root\cimv2\security\microsofttpm path win32_tpm get IsEnabled_InitialValue
Use the command below to determine if TPM is activated.
wmic /namespace:\\root\cimv2\security\microsofttpm path win32_tpm get IsActivated_InitialValue
SoftEther VPN Project
The SoftEther VPN Project is based from an university in Japan. It is a open-source cross-platform multi-protocol VPN application.
https://4sysops.com/archives/set-up-a-vpn-server-on-windows-with-softether-and-connect-clients/
https://www.softether.org
ZenMate
ZenMate is a plug-in for the Google Chrome browser that encrypts browser traffic through the company’s servers. It is currently free but appears will shift to a payment model in the future.
WinSetupFromUSB
WinSetupFromUSB is a Windows program which prepares multi-boot USB flash or fixed disk to install any Windows versions since 2000/XP, boot various Linux and BSD flavors.
How to quickly view the contents of a .CSV file using PowerShell
To quickly view a .CSV file using PowerShell, pipe the file in question to the Out-GridView cmdlet.
Import-CSV .\test.csv | Out-GridView -Title "CSV File"
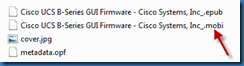
How to use a EPUB file with an Amazon Kindle
By default, an Amazon Kindle does not support the .EPUB format. One option is to convert the .EPUB file to a .MOBI format, which a Kindle supports. One application that can perform this conversion is called Calibre. A portable version for Windows can be found at:
http://calibre-ebook.com/download_portable
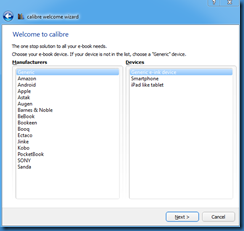
After extracting the program to a folder, launch the application. An initial setup wizard should appear asking for parameters such as language and the device. You can leave the device to generic.
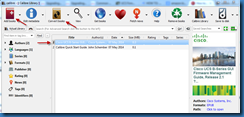
Use the Add Books button to select the .EPUB file in question. Select it in the list and then use the Convert Books button from the menu.
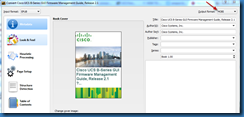
Select the output format of MOBI in the dialog box near the top right hand corner of the new dialog box, and click on the OK button at the bottom of the screen.
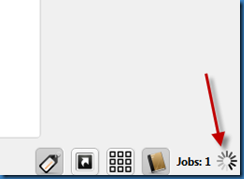
The job status progress should be displayed near the lower right-hand corner of the main dialog box.
Once completed, look under the Calibre Library subfolder to find the .MOBI version of the file.