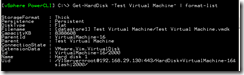
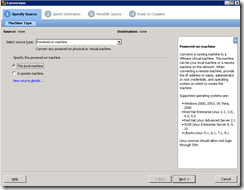
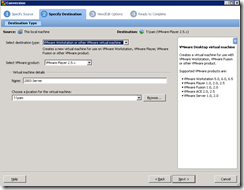
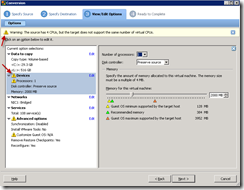
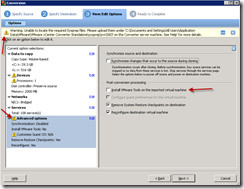
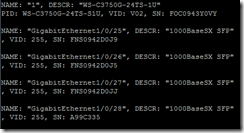
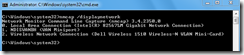
NMCap is a command-line executable that is included within Microsoft’s Network Monitor installation. It allows for network capture via a non-GUI method such as a batch file. The command nmcap /displaynetwork will show the available network cards.
The command nmcap /network * /capture /file C:\users\swalker\desktop\test.cap will capture all traffic on all network cards, and will place the data within a file called test.cap.
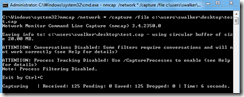
The command nmcap /network * /capture “tcp.port == 80” /file C:\users\swalker\desktop\test.cap will capture traffic only using TCP port 80 for all network cards, and will place the data within a file called test.cap.
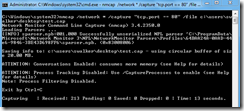
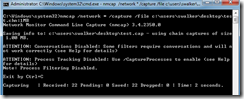
One option is to create capture files based on file size. This would prevent the creation of one large single file. The command nmcap /network * /capture /file C:\users\swalker\desktop\test.chn:1MB will capture traffic on all interfaces and create a series of 1 MB files.
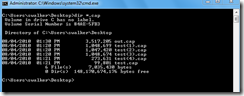
After using the command above, several separate files will be created after a period of time.
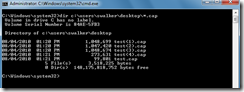
The individual files can be combined into a single file after the fact. The command nmcap /inputcapture test.cap test(1).cap test(2).cap test(3).cap test(4).cap /capture /file out.cap will combine the various individual files into one file.
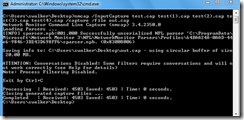
After the command is used, a new single file with all of the captured data should be present.
To see more sample options, use the command nmcap /examples. For example, the command nmcap /network * /capture (!ARP AND !ICMP AND !NBTNS AND !BROWSER) /File NoNoise.cap creates a capture file excluding several traffic types.